Appthority MTP Overview
Appthority MTP is a mobile threat defense solution that integrates with Enterprise Mobility Management (EMM) platforms to deliver enhanced capabilities for protecting mobile users and enterprise data. It provides on-demand cloud-scalability with continuous monitoring and real-time threat analysis, assessment, and remediation of potential and active mobile security threats to your enterprise. The MTP Mobile App provides additional on-device endpoint protection that helps employees self-remediate mobile threats while educating them on personal and enterprise security best practices.
This overview of the Appthority MTP product discusses core features and functionality, geared towards hands-on administrators and security professionals who implement and maintain the Appthority MTP system.
Threat Detection
Appthority MTP detects threats across multiple vectors using a combination of human investigation and automated analysis. Once the system is configured, Appthority MTP provides sophisticated mechanisms for identifying threats in the mobile environment.
Mobile Threat Vectors
Mobile devices are part of a mobile ecosystem that is subject to threats at every level:
- App: Apps and their backend data services are the primary source of mobile threats.
- Device: In addition to threats posed by the apps installed on devices, the devices themselves may be threatened by jailbreaking/rooting, untrusted certificates, and device configuration vulnerabilities, among others. Device threat detection requires the MTP Mobile App.
- Network: Mobile devices can be vulnerable to network-based, real-time attacks such as Man-in-the-Middle (MitM). Network threat detection requires the MTP Mobile App.
Appthority MTP detects threats across these major threat vectors.
MTT Researchers and Threat Analysis
The Appthority MTP platform pairs with the Mobile Threat Team (MTT), who are dedicated and experienced security researchers. The MTT researchers continuously look out for new threats, determine how to detect them, assign a severity or risk level, and consider how best to protect mobile device users from those threats. The research they gather is used by the Appthority MTP threat analysis and detection system to automatically respond to new threats in the mobile environment.
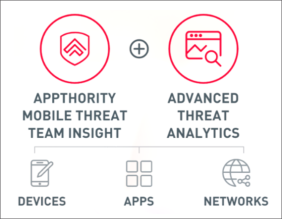
Threat analysis results are specified as Threat Indicators in the system, and app-level threats are described in detailed App Reports. The MTT researchers and Appthority MTP work together to provide well-investigated, dynamic, and automated mobile threat detection.
To arrive at this analysis, Appthority checks for hundreds of attributes, including:
- Internal and external API and web calls
- Third-party SDKs and libraries
- Location and timezone triggers
- Encryption protocols
- Jailbreaking or rooting
- Accessing and sending private data
- Malware and spyware
Threat Indicators
A Threat Indicator (TI) defines a specific app or device/network behavior that indicates a potential security risk. A TI is "detective" in nature, as it specifies particular conditions that may exist that indicate a particular threat. It can signify a risk to, an attack from, or a compromised situation. Since by definition a TI is always "A Bad Thing" then a TI also involves a level of risk. The MTT researchers create TIs, assign a risk level, and add them to the Appthority MTP system on an ongoing basis, where they become the building blocks for App and Device Policies.
The MTP Manager lists all the TIs in the system along with their assigned risk level, on a scale of 0-10. The listings show information about each TI and has links to more details about devices and apps that are currently exhibiting the TI behavior.
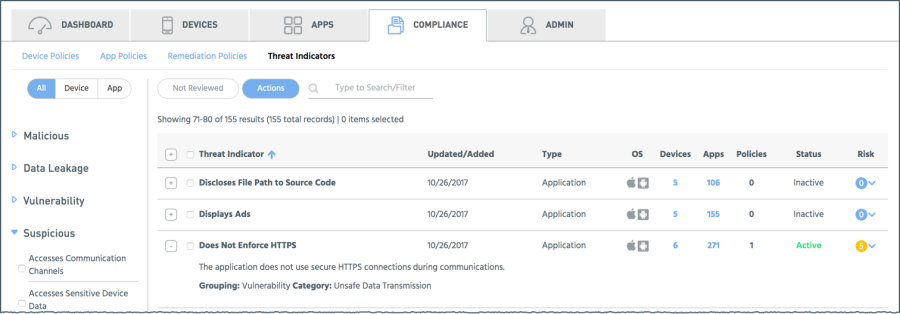
The MTT researchers arrange TIs into high-level groups such as Malicious, Data Leakage, Vulnerability, Suspicious, and Informational. Each group has categories that indicate more specific behavior, such as Malware or Insecure Data Storage. Multiple TIs may be listed in a group or category.
Mobile threats are many and diverse, and not every TI may be applicable to your company or division. You have the opportunity to review each non-Malicious TI and decide for yourself whether and how to use it.
Threat Management
Appthority MTP uses a combination of Threat Indicators, App and Device Policies, Remediation Policies and the MTP Mobile App, EMM integration, and MTP-Managed Policies to manage threats in the mobile environment.
App and Device Policies
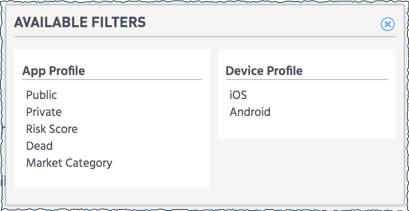
When you decide that a TI is important for your organization, you can activate it and assign it to an App or Device Policy. An App or Device Policy is composed of one or more TIs with optional policy filters. For example, an App Policy could use a TI that would apply to any app that sends data from the address book out over the network with improper encryption, and only to a single country, and only to a URL that has a low reputation score.
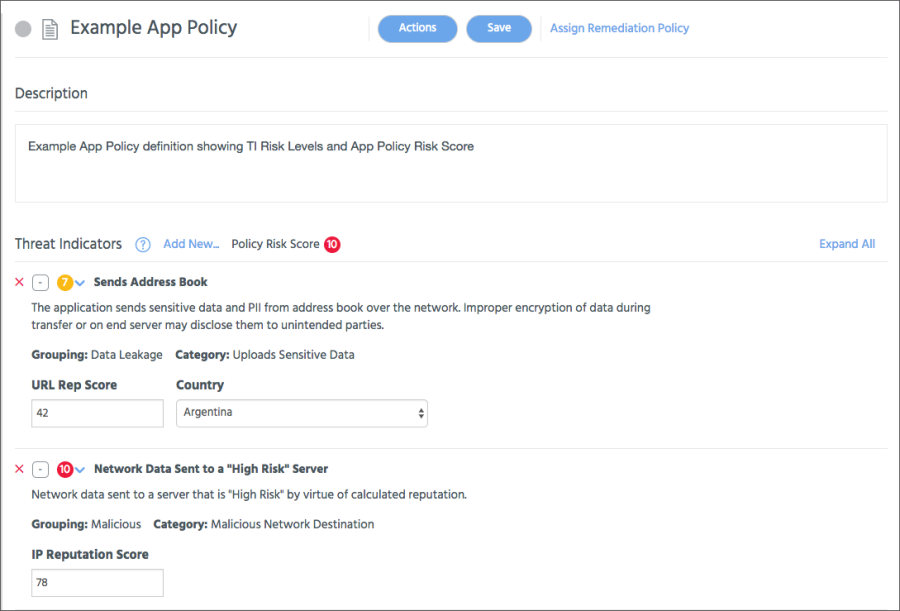
In addition to the TI parameters, you can narrow the scope of a policy by setting policy filters such as "only Private apps" or "only on Android devices".
Appthority MTP applies the policy criteria against the real-time state of the mobile device. When an app or device is found to meet the criteria, it is "in violation of the policy".
Device and Remediation Policies and the MTP Mobile App
Appthority MTP learns about devices and possible device-level threats from the MTP Mobile App on a user's device. You can create your own Device Policies using device-oriented TIs.
A policy violation can trigger one or more remediation actions, by escalating to an EMM for enforcement and/or by using the MTP Mobile App to request that users perform certain actions. You define remediation actions in the MTP Mobile App using Appthority MTP Remediation Policies.
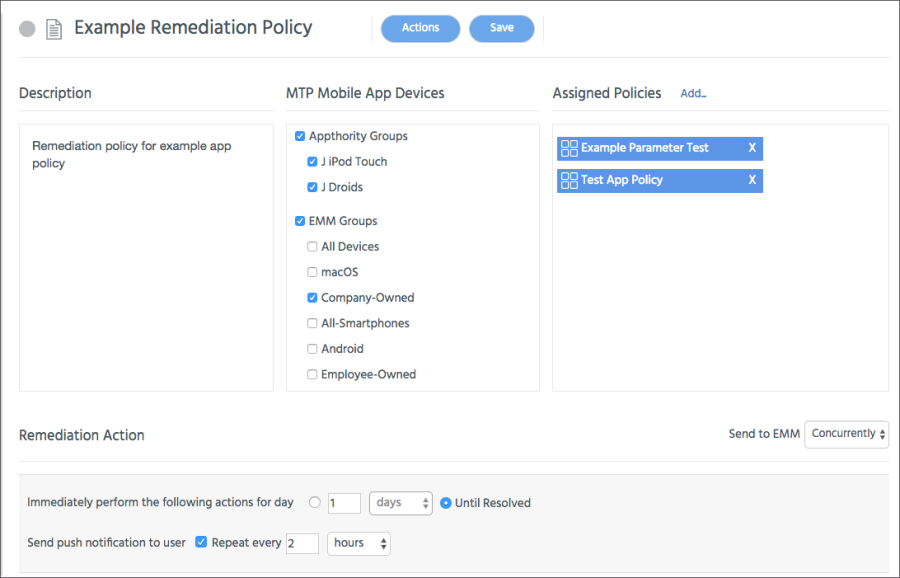
MTT-Managed Policies
Based on the severity or immediacy of a threat, a TI in the Malicious category is automatically activated as soon as Appthority adds it to the system. In addition, the MTT researchers proactively configure App, Device, and Remediation Policies that address high-level threats, called MTT-Managed Policies, and add those to the system. New MTT-Managed Policies immediately report on devices and apps that are under threat.
The MTP Manager Dashboard shows you the current Mobile Threat Team Updates and has links to any threatened devices or apps.
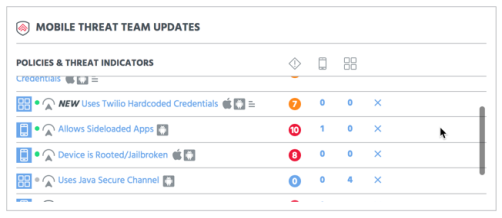
You can review both TIs and MTT-Managed Policies and, if needed, modify the pre-configured Remediation Policy and/or update how your EMM enforces policy violations. If for some reason you do not want to use or enforce an MTT-Managed policy, you can deactivate its Remediation Policy or change some of its remediation actions.
TI Risk and Risk Scores
With so many possible threats, Appthority MTP provides scoring to help sort through and prioritize them. TI Risk (also called Risk Level) is the basis for scoring policies and apps.
The MTT researchers assign each Threat Indicator a Risk that reflects the potential risk of a violation, on a scale of 0-10. For ease-of-use in the MTP Mobile App app, these are described as High/Med/Low.
For a discussion of how risk scoring works in Appthority MTP see Risk Scoring.
EMM Integration
Appthority MTP integrates with leading EMM software to provide additional app inventory and policy enforcement actions. Integration is accomplished using the EMM Connector.
App Inventory
On a dynamic ongoing basis, apps are detected and analyzed by Appthority MTP and the MTT researchers. Analysis status displays in the Apps tab.
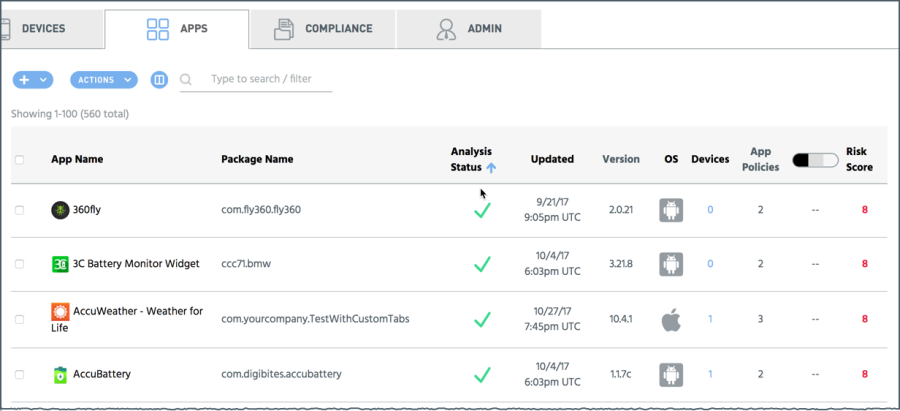
Appthority MTP can maintain an inventory of the apps on your user's devices, or other apps that are of interest to you, and analyze them to provide a great deal of information about the apps and any possible threats that they pose. You can correlate the apps with the devices to find out exactly what users are affected.
The app inventory can be populated in three ways:
- From existing information in an EMM, using the EMM Connector
- By manually uploading app metadata or binaries
- From a URL
- From the MTP Mobile App
Escalated Policy Enforcement
EMM integration allows policy violations to be communicated to the EMM so that the EMM can perform its own remediation and enforcement activities.
MTP Mobile App Deployment
The MTP Mobile App can be deployed and managed using EMM capabilities. This helps centralize the management of apps on your company's mobile devices.
Threat Intelligence
Appthority MTP continuously monitors the apps and devices in your mobile environment and reports back to you with Dashboard data and email notifications.
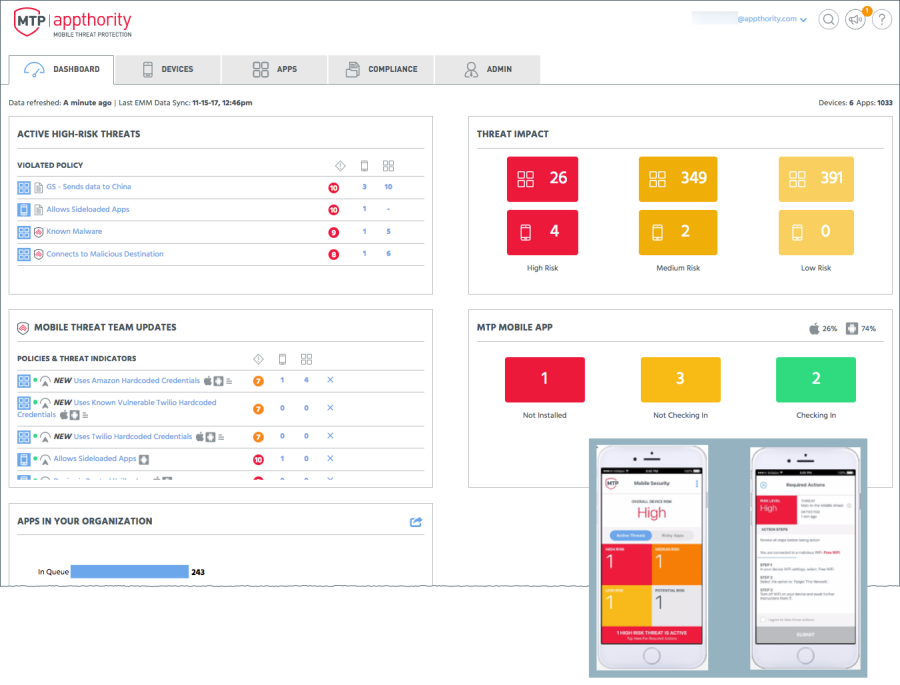
Dashboard
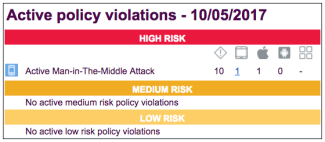
Appthority MTP provides a mobile threat Dashboard that helps you quickly identify and pinpoint where problems exist. The Dashboard correlates policy violations down to a specific app or user device.
For details about the Dashboard see Dashboard for Quick Status.
Email Alerts for Policy Violations
Appthority MTP can send email alerts when compliance policies are violated.
A policy violation email alert has links that take you to the relevant policy.
Copyright ©Appthority, Inc. 2017-2018 All Rights Reserved. Contact Support